1、安装openssl
wget https://www.openssl.org/source/openssl-1.1.1b.tar.gz
./config --prefix=/usr/local/openssl --shared
--shared为添加动态库,生成libssl.so,默认只有libssl.a静态库
make
make install
ln -s /usr/local/openssl/bin/openssl /usr/bin/openssl
cp /usr/local/openssl/lib/openssl/libssl.so.1.1/lib/x86_64-linux-gnu/
cp /usr/local/openssl/lib/openssl/libcrypto.so.1.1 /lib/x86_64-linux-gnu/
2、新建jni工程(eclipse为例)
新建java工程PemCheck
src下新建class com.jni.OpenSSLUtils.java
package com.jni;
public class OpenSSLUtils {
public native static int checkPem(String pem,String key);
}
cd ${workspace}/PemCheck
javah -classpath . -d . com.jni.OpenSSLUtils
javah -jni com.jni.OpenSSLUtils
此时src下生成com_jni_OpenSSLUtils.h头文件
/* DO NOT EDIT THIS FILE - it is machine generated */
#include <jni.h>
/* Header for class com_jni_OpenSSLUtils */
#ifndef _Included_com_jni_OpenSSLUtils
#define _Included_com_jni_OpenSSLUtils
#ifdef __cplusplus
extern "C" {
#endif
/*
* Class: com_jni_OpenSSLUtils
* Method: checkPem
* Signature: (Ljava/lang/String;Ljava/lang/String;)I
*/
JNIEXPORT jint JNICALL Java_com_jni_OpenSSLUtils_checkPem
(JNIEnv *, jclass, jstring, jstring);
#ifdef __cplusplus
}
#endif
#endif
3、新建C++工程(eclipse为例)
new project >>C++ Project >> ShardLibrary
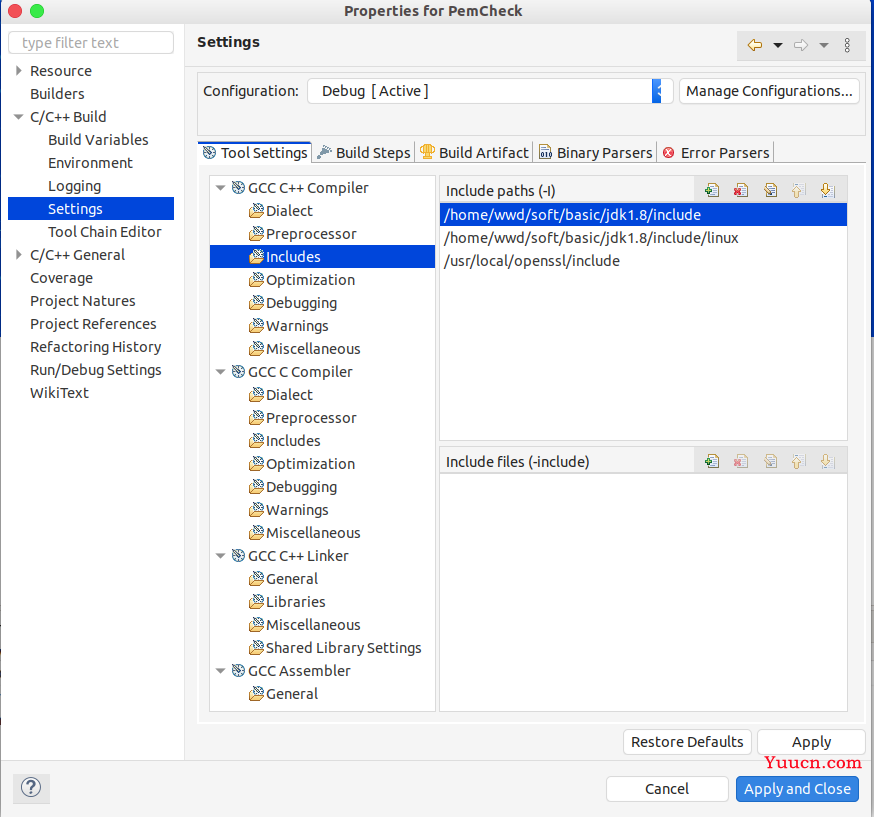
设置编译环境
include jdk的头文件path
include jdk的头文件 linux path
include openssl 头文件path
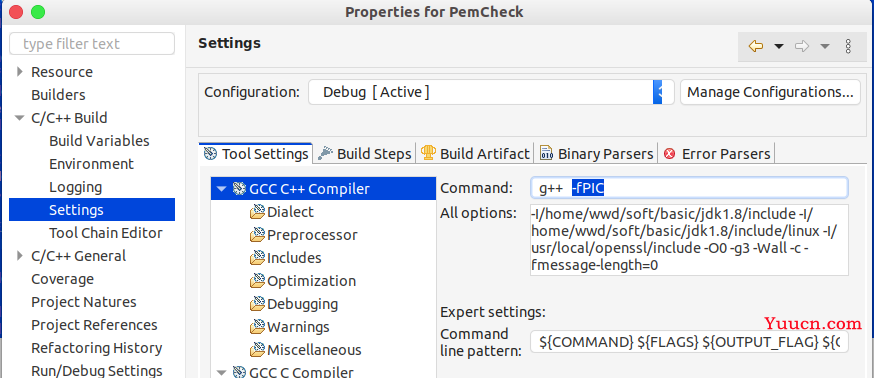
编译参数加上-fPIC
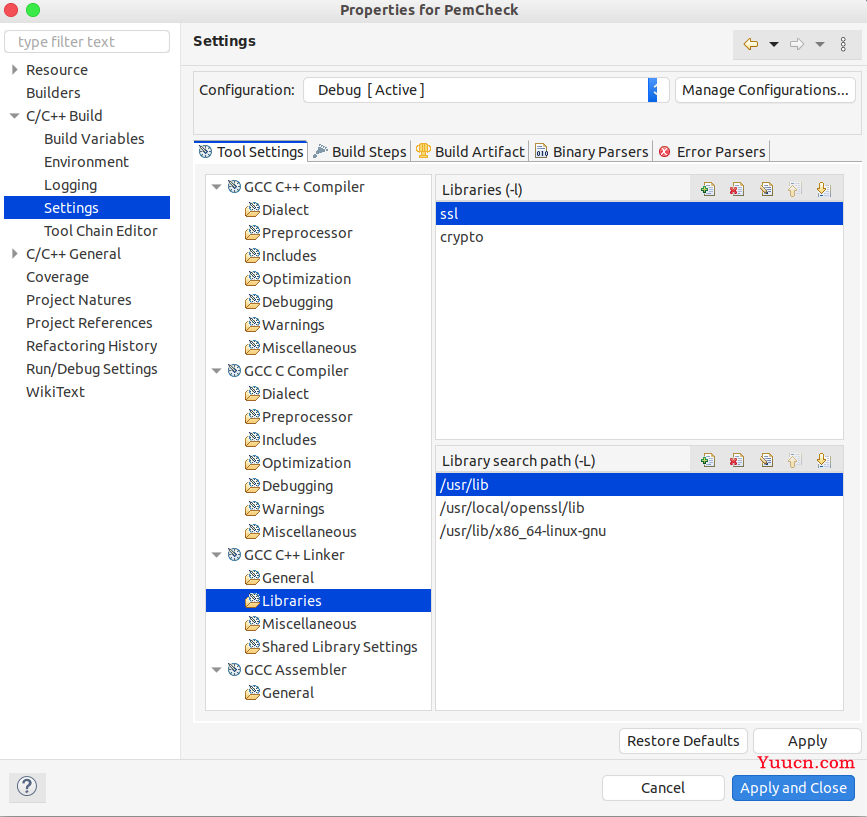
链接库加上ssl,crypto
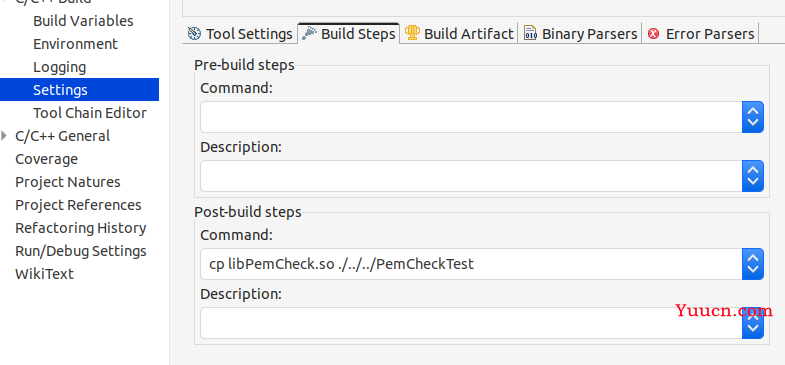
可以配置个命令将编译后的so库cp到测试或使用的工程路径下
4、编写openssl检测代码
新建src文件夹,将com_jni_OpenSSLUtils.h复制到该目录下,
同时新建com_jni_OpenSSLUtils.cpp
#include "com_jni_OpenSSLUtils.h"
#include "openssl/pem.h"
#include "openssl/bio.h"
#include "openssl/ssl.h"
#include <iostream>
using namespace std; // @suppress("Symbol is not resolved")
/*
* Class: com_jni_OpenSSLUtils
* Method: checkPem
* Signature: (Ljava/lang/String;Ljava/lang/String;)I
*/
JNIEXPORT jint JNICALL Java_com_jni_OpenSSLUtils_checkPem
(JNIEnv *env, jclass jc, jstring pem, jstring key){
BIO* keyBIO;
EVP_PKEY* pkey;
BIO* pemBIO = BIO_new_mem_buf(env->GetStringUTFChars(pem,0),-1);
X509* cert = PEM_read_bio_X509(pemBIO,NULL,NULL,NULL);
if (cert == NULL) {
cout << "PEM_read_bio_X509_AUX() failed" << endl;
if(NULL != pemBIO)
BIO_free(pemBIO);
return -1;
}
keyBIO = BIO_new_mem_buf(env->GetStringUTFChars(key,0),-1);
pkey = PEM_read_bio_PrivateKey(keyBIO,NULL,NULL,NULL);
if (pkey == NULL) {
cout << "PEM_read_bio_PrivateKey() failed" << endl;
if(NULL != cert)
X509_free(cert);
if(NULL != pemBIO)
BIO_free(pemBIO);
if(NULL != keyBIO)
BIO_free(keyBIO);
return -1;
}
SSL_library_init();
OpenSSL_add_all_algorithms();
SSL_load_error_strings();
SSL_CTX* ctx = SSL_CTX_new(SSLv23_client_method());
if (ctx == NULL) {
cout << "ctx create failed" << endl;
goto bad;
}
if(SSL_CTX_use_certificate(ctx,cert)<=0){
cout << "user certificate fail" << endl;
goto bad;
}
if(SSL_CTX_use_PrivateKey(ctx,pkey) <=0){
cout << "user key fail" << endl;
goto bad;
}
if(!SSL_CTX_check_private_key(ctx)){
cout << "key does not match the certificate" << endl;
goto bad;
}
if(NULL != pemBIO)
BIO_free(pemBIO);
if(NULL != keyBIO)
BIO_free(keyBIO);
if(NULL != pkey)
EVP_PKEY_free(pkey);
if(NULL != cert)
X509_free(cert);
if(NULL != ctx)
SSL_CTX_free(ctx);
return 0;
bad:
if(NULL != cert)
X509_free(cert);
if(NULL != pemBIO)
BIO_free(pemBIO);
if(NULL != keyBIO)
BIO_free(keyBIO);
if(NULL != pkey)
EVP_PKEY_free(pkey);
if(NULL != ctx)
SSL_CTX_free(ctx);
return -1;
}
Build All.
5、测试
在java工程下新建Test 类
package com.jni;
public class Test {
static {
System.load("${solibpath}/libPemCheck.so");
}
public static void main(String[] args) {
System.out.println(
OpenSSLUtils.checkPem("-----BEGIN CERTIFICATE-----\n"
+ "MIIDUDCCAjgCCQDcSSulgrGudTANBgkqhkiG9w0BAQsFADBqMQswCQYDVQQGEwJD\n"
+ "TjERMA8GA1UECAwIWmhlamlhbmcxETAPBgNVBAcMCEhhbmd6aG91MQ4wDAYDVQQK\n"
+ "DAVtb2ZlaTEOMAwGA1UECwwFbW9mZWkxFTATBgNVBAMMDHd3dy50ZXN0LmNvbTAe\n"
+ "Fw0yMjEyMjEwNzMzNTVaFw0zMjEyMTgwNzMzNTVaMGoxCzAJBgNVBAYTAkNOMREw\n"
+ "DwYDVQQIDAhaaGVqaWFuZzERMA8GA1UEBwwISGFuZ3pob3UxDjAMBgNVBAoMBW1v\n"
+ "ZmVpMQ4wDAYDVQQLDAVtb2ZlaTEVMBMGA1UEAwwMd3d3LnRlc3QuY29tMIIBIjAN\n"
+ "BgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAzqAHiN+76XHpcBIQKzT4+a7L/kI5\n"
+ "cBeNr07Z0E/9zy9a0k5iVD+4boFk22yGPyoukGWZWnrK0yehAHG4WqEt5FKb8wms\n"
+ "FEumnscPDmlq1jE+nuRfudUCyJU1PqdfkP4bI34ZKsgH9wiHONmqYAHJaAZtQTbn\n"
+ "EfWszFEJ4Mjyv/WStN0YX3K2vUjzvvB891oR5YF6WblawG1EqK+qZKtNEOVA5mVQ\n"
+ "YvTysbPd0dAV6VhDIcdagWSeF4y0f8BOlKrJyEKwiy6b/Mvl6ewf1/aRVF/qa4DV\n"
+ "scQtg88TDKrmwaKJR4cSfo5JYDw8kkuuuFNazFkqlT6mcWeOrdx+awH1SwIDAQAB\n"
+ "MA0GCSqGSIb3DQEBCwUAA4IBAQAab5Fl9DNimm3gXdhrOpo8+Gjy9OEon/jy16uF\n"
+ "SyzOpo45U3r7rtkSSKuQOJZ5VDv3gtBKjVGhFSwbIEHAYVWg8qOliLq2LHAkWwFd\n"
+ "eN0jVD2/cxjJMhQP7fbfYVLy7mHBp3zQ72uni3EzcjLYTc3Ly45TAko292MjTYcW\n"
+ "uEkwp1NQiZklFnncXdJIx1vJ+TPweUi66iJk1FYJwkDcQV69GDLO9RnqMUsNHIRo\n"
+ "q6JvvIBZ+VT8qY5TQ2nxHaWnN/55Iq/5gvZ1XI6J05oTughX0ojSRNfdzGVC8Yg2\n"
+ "US8cG6NTgx8c1AFl1PA3vb8yGcgvESQIhS5tH60UOnVLVuT4\n"
+ "-----END CERTIFICATE-----\n"
+ "","-----BEGIN RSA PRIVATE KEY-----\n"
+ "MIIEpAIBAAKCAQEAzqAHiN+76XHpcBIQKzT4+a7L/kI5cBeNr07Z0E/9zy9a0k5i\n"
+ "VD+4boFk22yGPyoukGWZWnrK0yehAHG4WqEt5FKb8wmsFEumnscPDmlq1jE+nuRf\n"
+ "udUCyJU1PqdfkP4bI34ZKsgH9wiHONmqYAHJaAZtQTbnEfWszFEJ4Mjyv/WStN0Y\n"
+ "X3K2vUjzvvB891oR5YF6WblawG1EqK+qZKtNEOVA5mVQYvTysbPd0dAV6VhDIcda\n"
+ "gWSeF4y0f8BOlKrJyEKwiy6b/Mvl6ewf1/aRVF/qa4DVscQtg88TDKrmwaKJR4cS\n"
+ "fo5JYDw8kkuuuFNazFkqlT6mcWeOrdx+awH1SwIDAQABAoIBAG5Fub+yp/bOdGb7\n"
+ "POXSP44BW502erD34QXObzBdgHcyLqZObuvHlgZjyA/Su1K6kF8/2bgQEG7gl2xF\n"
+ "RL4ZhwRzkgcDAnNSbHoQgliOqhXl8iWae/wRUor6FpB5guc+tf0bLxNF7fpI8uHE\n"
+ "SMk0Kuj5hRVo16keFDp2hW8Rz3vh/VysAjnNuG3Gofvk1TbuEeF15eaLv7k+rZJV\n"
+ "KoFQ9cbTZD7LZPifimqBjuhCQVpsEfi8vbHidg+W7i+zt5L6e2o2Nc8X4CJE3vAs\n"
+ "MNGkyxrgR5M+uneOz4+WsuNxwx6YiIPXKYr+kOJvze7sAV0OYNtJVwFHzvmxfQ79\n"
+ "0XqtxQECgYEA99vSozDexH5Fh7SG+GlTFgzlw4BrmHUv2DyRpXz+ceJdfokHXFfX\n"
+ "SRCkH0axFQ2U60Iyv/W9oACXtKFHfLOj/fPczA0w7661rF1ANHmrMcodMdE27FcU\n"
+ "joGe0d2Wj2SnGr4JtqxnZDS/GFJfwQxTpLEI0js6eaK1PRi/krFzB80CgYEA1Wl8\n"
+ "D7kePEq7KujegF6w9hx5du708c21/usLEhdBLmOhcTE4N3f+fUnYSG0D/3o68BRn\n"
+ "8CmDkUfQPltLy/l8vJI4OE2kUxxlYa5RRRbvHX47cUHxRuDTK40Ip1iAgHc/EZRE\n"
+ "HJD65HW7FuiaTSqYb8VIA3ywcLg1UGhqNY7vqXcCgYEAwy3/uTKKugEVj7/BaWzH\n"
+ "WN3fMQy3rd7aRlWr+71qQRQYu8P8X+NsTMUl+NsaJ5ICayA+BpvlL1JIJJ28RZ7Q\n"
+ "zPJ0NNtOZfAWcB0eqjQFc7fNNaWisooAThgUkP8FyPViAdUUoR0ybd57fROhA8xJ\n"
+ "Ma+XWrX5Xj+aqPoMIeBKzSECgYAhLdYw55nwy7mPsUaudIpUqRalS/9e/Jl3+Xju\n"
+ "JhlnKew2me1gilJRjkKG+BPwC0PQgYurRfkDhEO2/iCppK8k7iK5djC/DyIf7qcJ\n"
+ "88fXMQHy2Mq3N0r9cV7QDa1ky6VNiVyRiGTJUhh1NlKO/rlWXziT+jXAQJNhXept\n"
+ "SzytfwKBgQC72ceWLWFBo0uAVPWmxFtOKVUZOY2tN3FwLUQkEt52F+VU2vhrKnpu\n"
+ "Ja+CRxA0ZycKg8EDYpJA+xFc7GBWZtsfI2iEN2/gH1x96sctmGbyJec9Ws36RqPb\n"
+ "VgXM+Y6VobyMIOKyJzs/Upz5+3btRToAfUJw5wnThh9zOAIM+VGNxg==\n"
+ "-----END RSA PRIVATE KEY-----"));
}
}